CloudVDI Cloud Personal
The Workspace Streaming Platform
Stream your workspace directly to your web browser on any device and from any location.
Try it Now
As you saw us in:
Solutions For Your Workspaces Needs
- Cloud Desktop
- Web Isolation
- OSINT
- Remote Access
- Enterprise Browser
- App Streaming
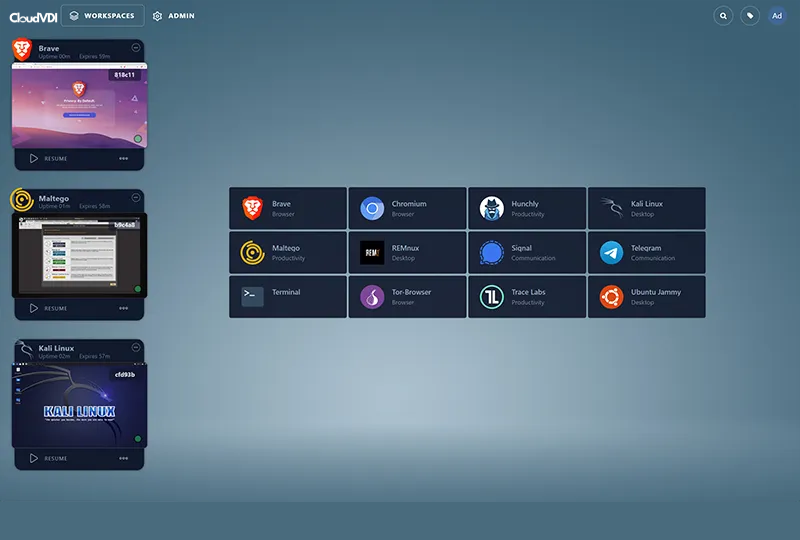
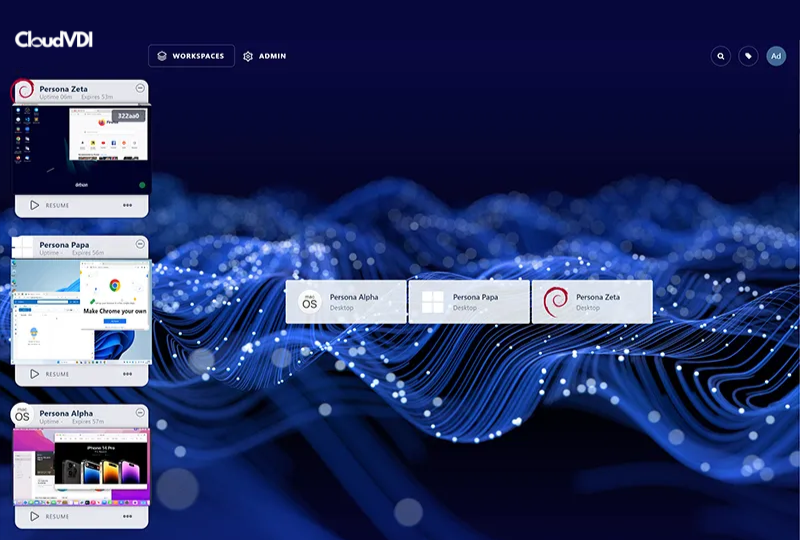
CloudVDI Desktops on Demand
Browser-based access to a secure and customized work environment. Work from any location on any device.
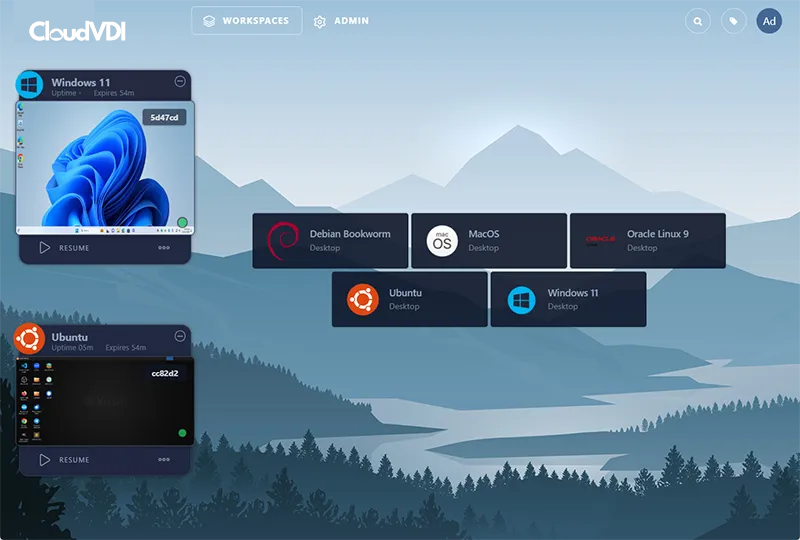
Desktop as a Service
Desktop access in seconds – infinitely scalable and delivered securely through the web browser. Side-by-Side support for Windows, Linux, MacOS, Android, and more (Including GPUs).
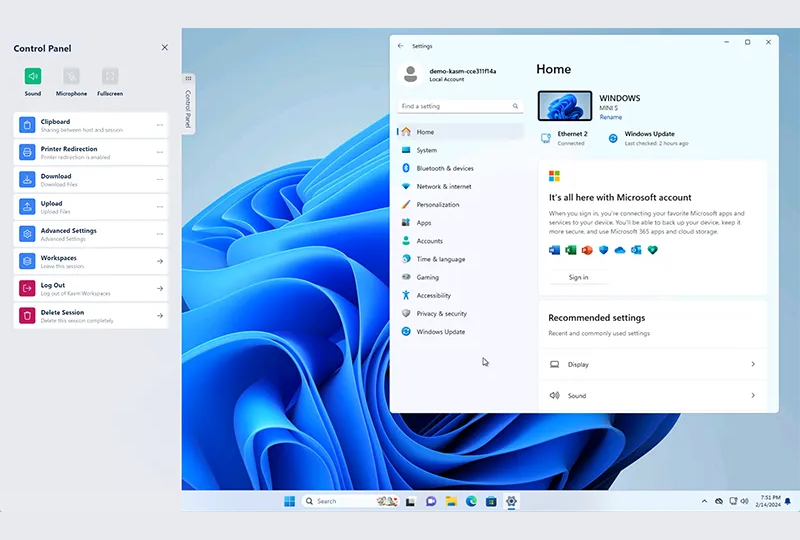
Windows Desktops
Windows Enterprise deployments – including Microsoft Remote Desktop Servers (RDS), Azure Virtual Desktops (AVD), Fixed Servers running Remote Desktop Protocol (RDP) to Autoscaled Cloud (AWS, Azure, GCP, OCI) and On-Prem (VMWare ESXi and OpenStack)

Linux Desktops
Containerized Desktop Infrastructure® (CDI) running on a shared Linux kernel for lightning fast boot times, less compute, memory and disk space. Develop pipeline automation streamlines security patches, software updates and maximizes performance.
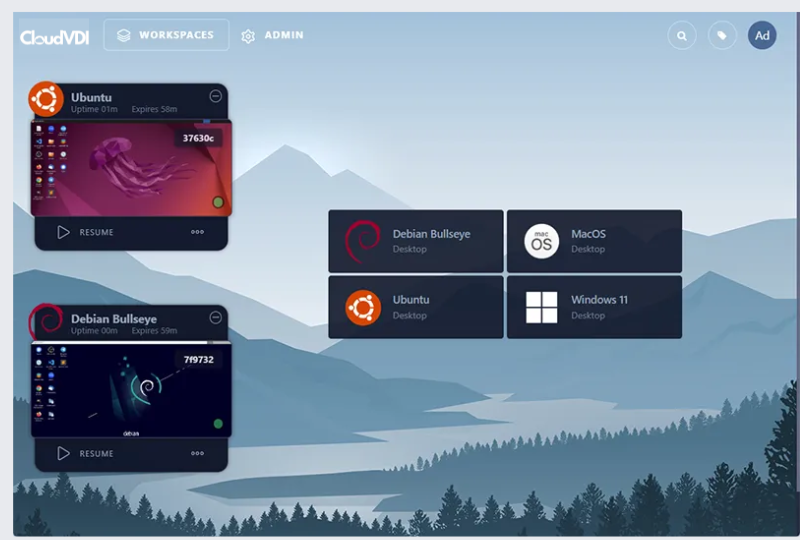
Desktop as a Service
Our Desktops are built to solve complex business challenges, such as hot desking, frontline desktops, application casting and legacy application support. We also support the transition from traditional desktop applications to web services, including O365.
Browser Isolation & Web Gateway
Zero-Trust Secure Web Intermediary to keep your endpoints safe while browsing the Internet.
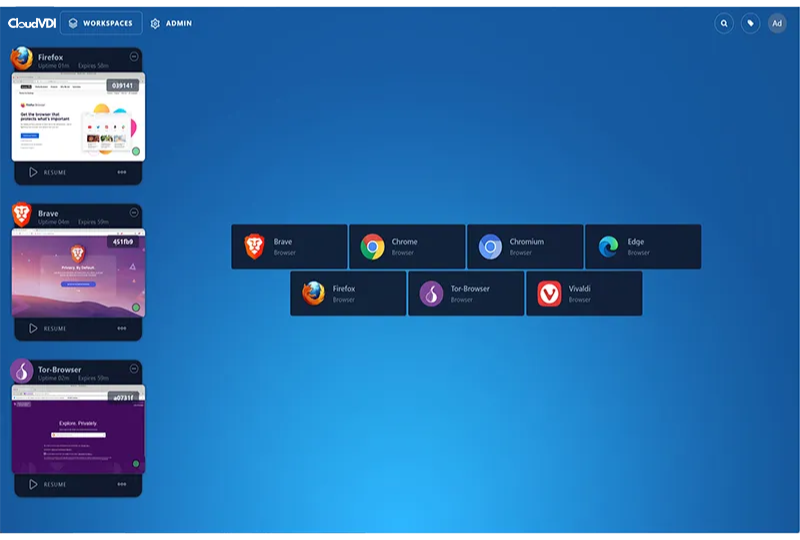
Browser Isolation
A remote, containerized browser that is rendered inside the user’s local browser serving as a secure intermediary that tightly controls what data is allowed to be brought into our allowed out of the network. This is the ultimate protection from viruses, ransomware, and other types of malware complimented by absolute control of data loss prevention.
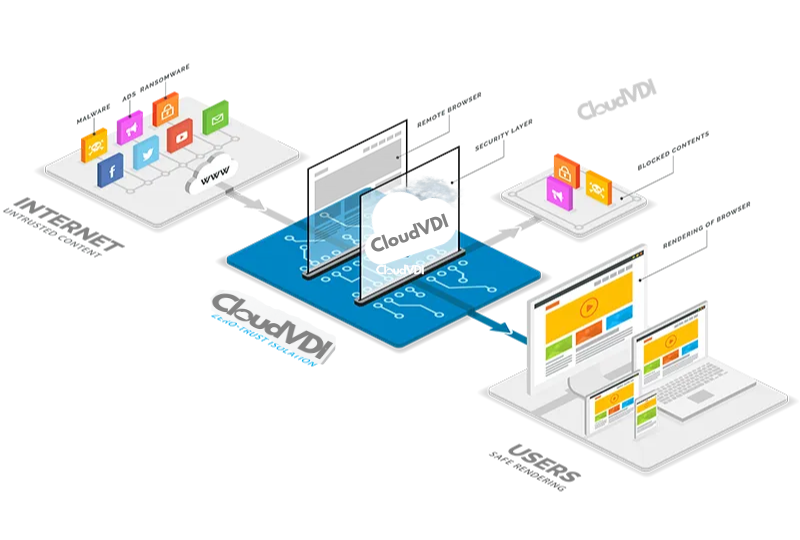
Enterprise Web Gateway
Move the risk of web threats outside of your organization with our transparent web redirects. Your users will feel as if they are experiencing the web firsthand, however, since web content never directly interacts with the user’s endpoint, your enterprise is protected against malware and your data remains safe.
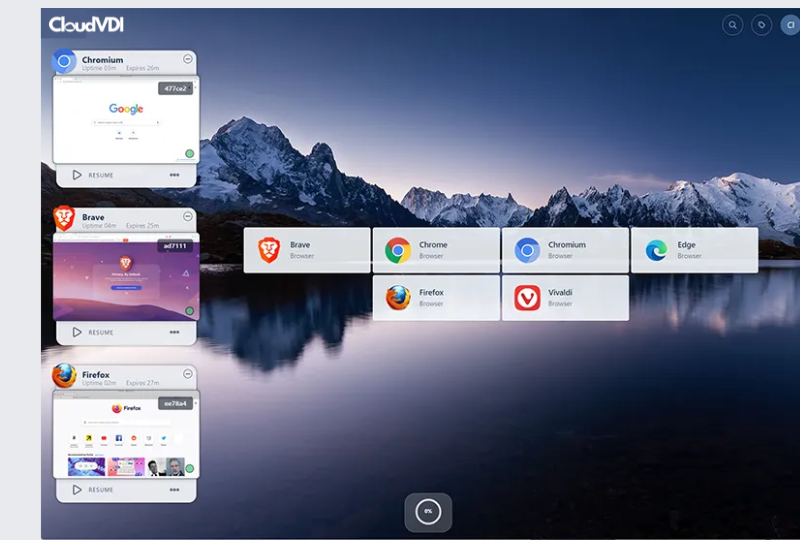
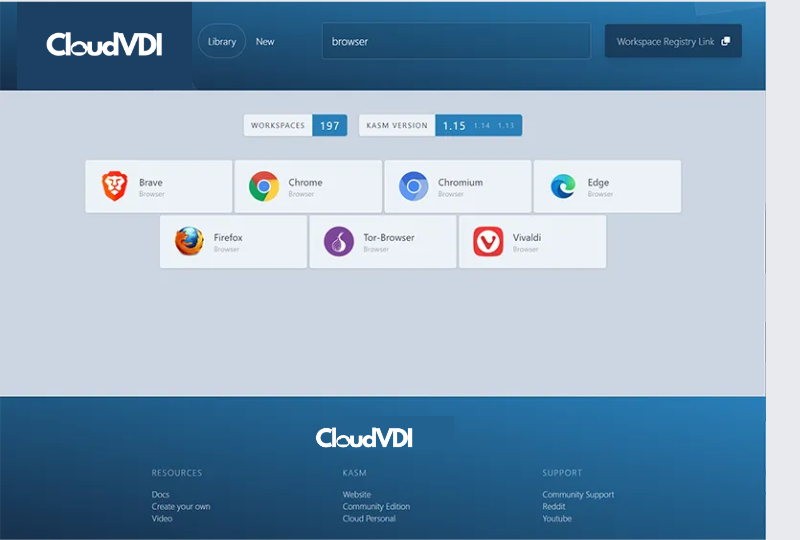
CloudVDI Cloud Browser
Our Zero-Trust Browser Isolation SaaS. Keep your web browsing secure, private, and non-attributable with no risk of compromising your endpoint. A fully-patched, disposable browser that is destroyed after each use, eliminating all traces of malware, tracking cookies, browser history, browser caching, and session fingerprints.
Enterprise Zero Trust Web Access
One of the biggest security risks to organizations is direct internet access to the endpoint. Employees typically need access to the internet to do their jobs, but the proliferation of viruses, malware and phishing attacks pose a significant risk. Browser Isolation categorically removes this risk, by shifting the paradigm of how this internet is accessed.
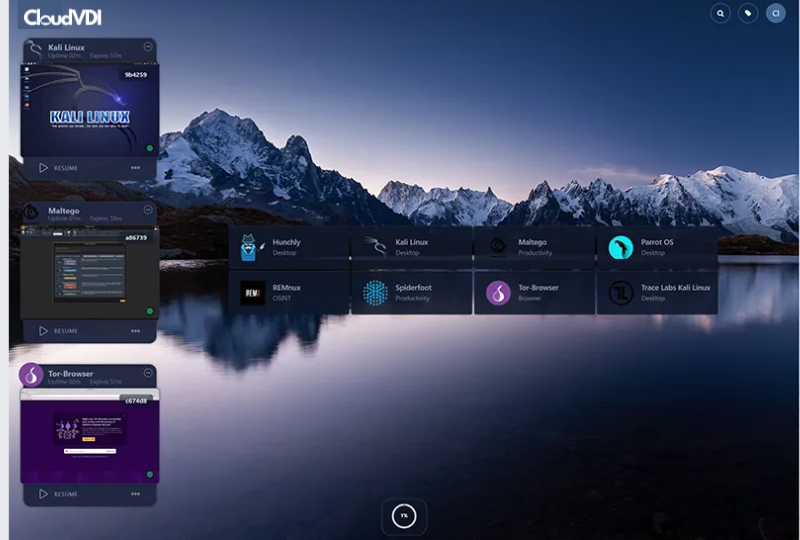
Open-Source Intelligence
Secure and anonymous web browsing for non-attributable open-source intelligence (OSINT).
Secure & Anonymous Research
A remote, containerized browser that is rendered inside the user’s local browser serving as a secure intermediary that tightly controls what data is allowed to be brought into our allowed out of the network. This is the ultimate protection from viruses, ransomware, and other types of malware complimented by absolute control of data loss prevention.
Managed Attribution
Zero-Trust Web Intermediary where all web interactivity is executed in docker containers running in an anonymous public cloud. The remote CloudVDI cloud environment is destroyed after each session, ensuring system or network-based methods of tracking/identifying users cannot persist to the next user session or ever be traced to the origin.
CloudVDI Cloud OSINT
Our Open Source Intelligence and Web Research SaaS. A zero-trust web intermediary providing security and anonymity while using research and intelligence collection tools.
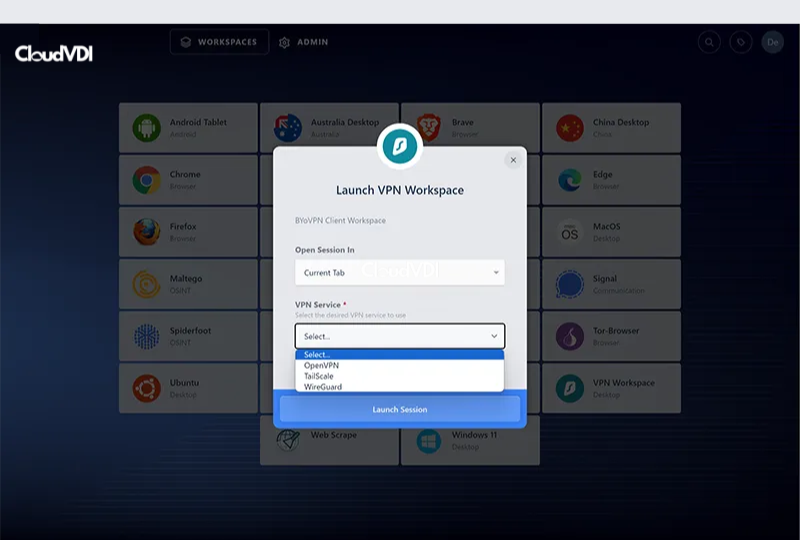
Enterprise VPN Egress
One of the biggest security risks to organizations is direct internet access to the endpoint. Employees typically need access to the internet to do their jobs, but the proliferation of viruses, malware and phishing attacks pose a significant risk. Browser Isolation categorically removes this risk, by shifting the paradigm of how this internet is accessed.
Zero-Trust Remote Access
Secure Browser-Based DLP-Protected Access to Remote Enclaves and Applications.

Secure Gateway to Enterprise Resources
Access your corporate resources, applications and data from remote locations without the risk of malware or data access. Remove the endpoint from your attack surface and prevent the loss or compromise of your sensitive data.
Network Segmentation
CloudVDI eliminates the risk of direct attacks on the internal network by serving as secure, controlled bastion host providing network segmentation and only allowing rendering of the workspace to exit the environment.

Remote Administration
Secure remote administrative access to internal resources with no agent or browser plugin required. Since direct network access is not provided, the endpoint can be untrusted (Including BYOD), preventing the need for a VPN, host integrity checks and endpoint protection software.

Regulatory Compliance
Meet Federal/Industry compliance requirements for data handling regulations/policies by keeping all data and applications resident within your existing infrastructure.
Enterprise Browsing & Compliance
A secure, accessible and compliant virtual browsing solution for protecting endpoints and data.
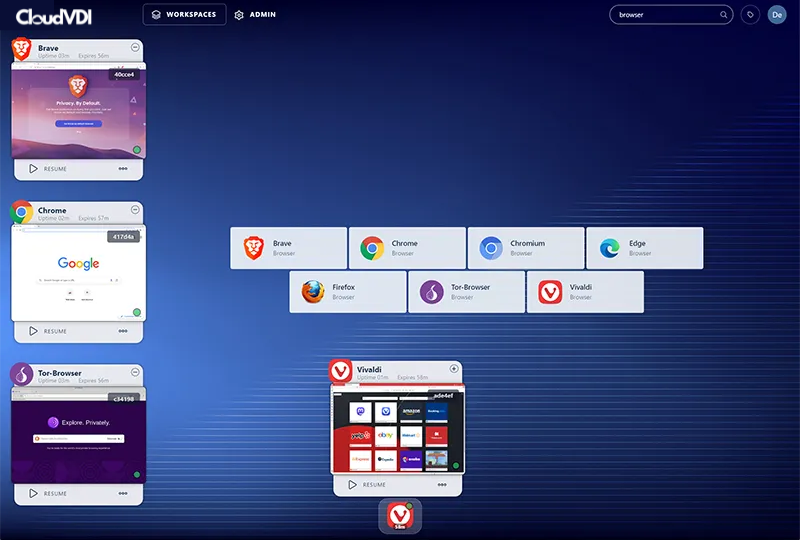
The Browser is the Application
Our “Virtual Browsing” remote container strategy isolates activity away from the device and securely accesses it from the cloud. Your virtual browsing activities are securely streamed to your local browser. Advanced security features to protect against threats like phishing, malware, and data breaches.
Protection from Malware and Data Loss
The Enterprise Browser is sandboxed in a self-contained environment. No worries about compromising your local device. No worries about infecting the corporate network. Malware has no place to go. It is isolated in the container, so your data stays safe.
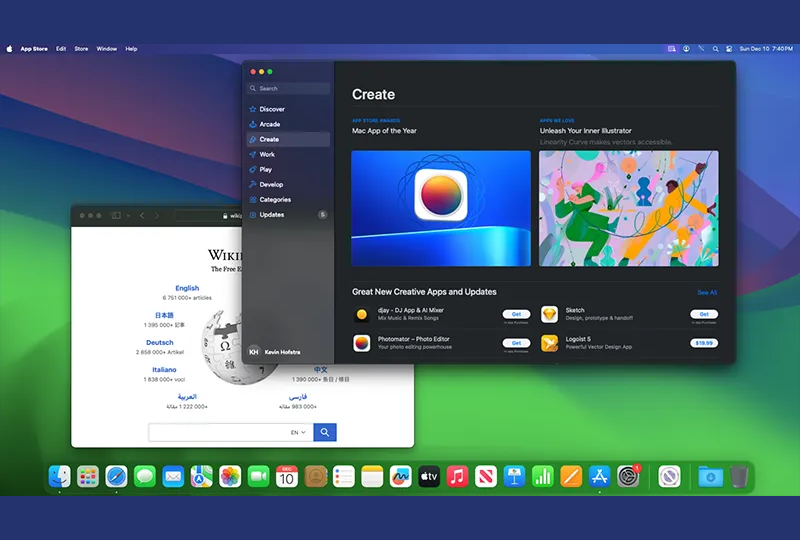
Cross-Platform Support
Available across different operating systems and devices, allowing for a seamless experience from a PC, Mac, or mobile device. Support for legacy web applications that may not function correctly in consumer browsers, ensuring continued access to critical business tools.
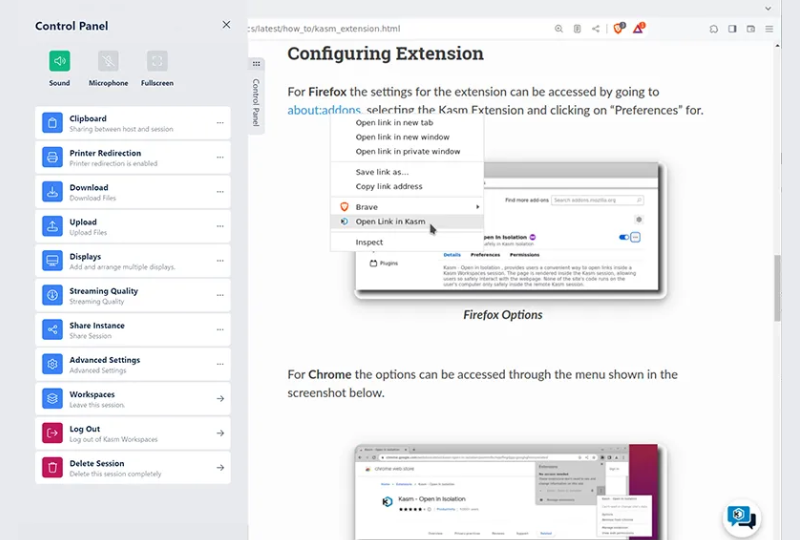
Compliance and Consolidated Management
Centrally manage enterprise browsers, including deploying updates, configuring settings, managing extensions, and enforcing compliance with company policies. Integration with tools like single sign-on systems, backend infrastructure, and internal company portals, streamlining workflows and improving efficiency.
Application Isolation and Streaming
Zero-Trust hosting of legacy applications without putting your environment at risk.
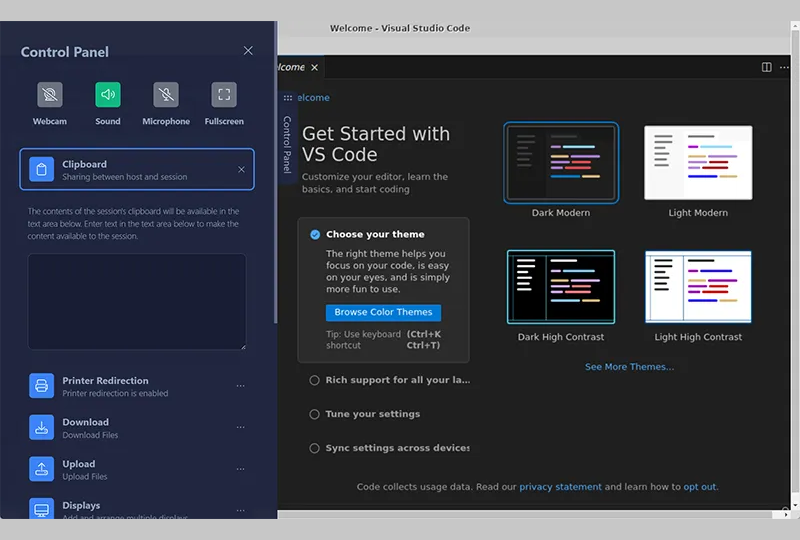
Application Streaming
Access applications directly from your browser, no install, no maintenance. Updates and patches are applied centrally to the streamed applications, reducing licensing costs, decreasing hardware requirements and ensuring all users have the most current version without individual updates.
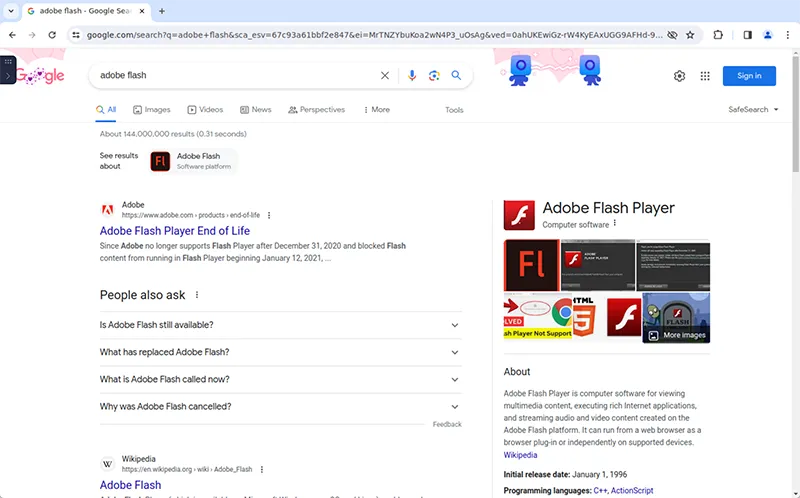
Legacy Applications
Securely host legacy applications, such as Adobe Flash, outdated versions of Java, and more, in a secure remote sandbox. A rendering of the application is transmitted to the user’s browser. This ensures the users’ systems are kept secure and organizations can continue to operate legacy applications while not compromising on security.
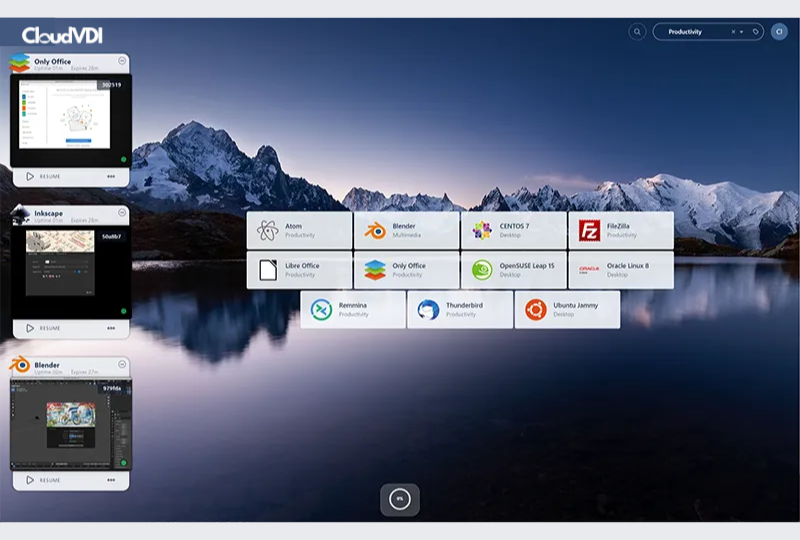
Cloud Personal App Streaming
Application access in seconds – on any device, from any location, securely through the web browser. Access applications from anywhere with internet connectivity, supporting remote and mobile workforces.
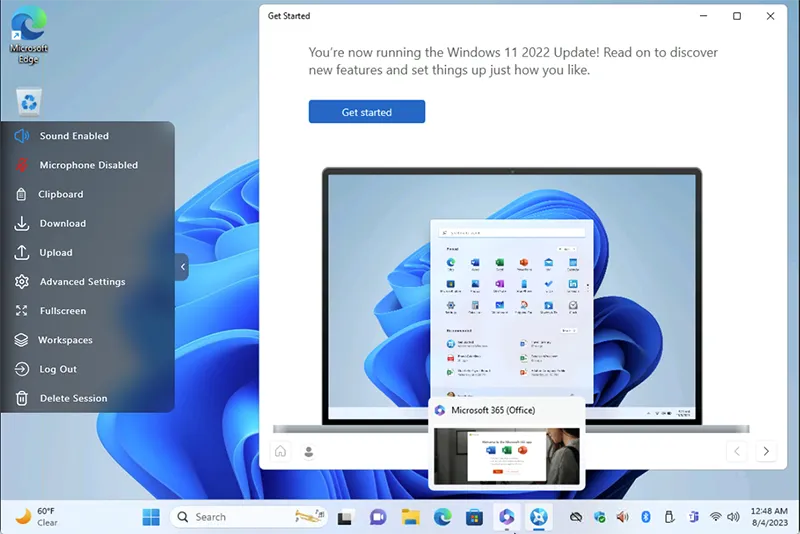
Windows Remote App
Simplified management of your digital footprint for privacy-conscious users, businesses that handle sensitive data, and professionals involved in security and intelligence operations. Protect your identity, bypass geo-restrictions/censorship, and maintain the security/privacy of your analysts.
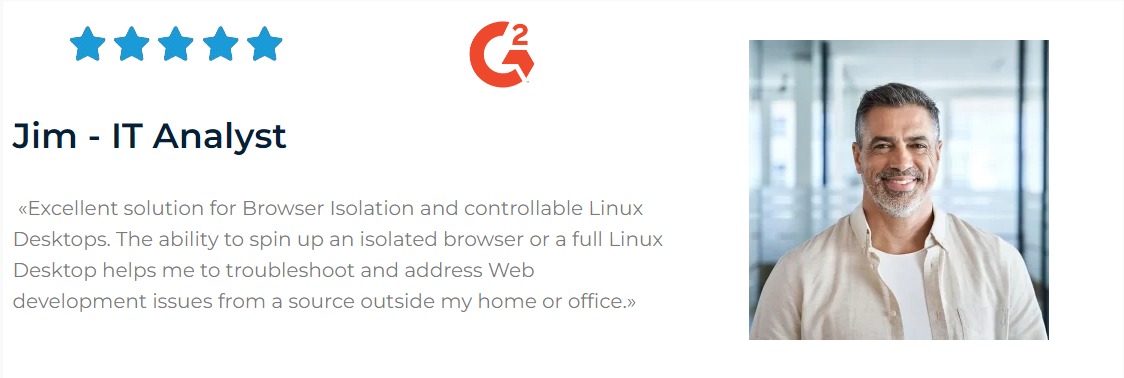
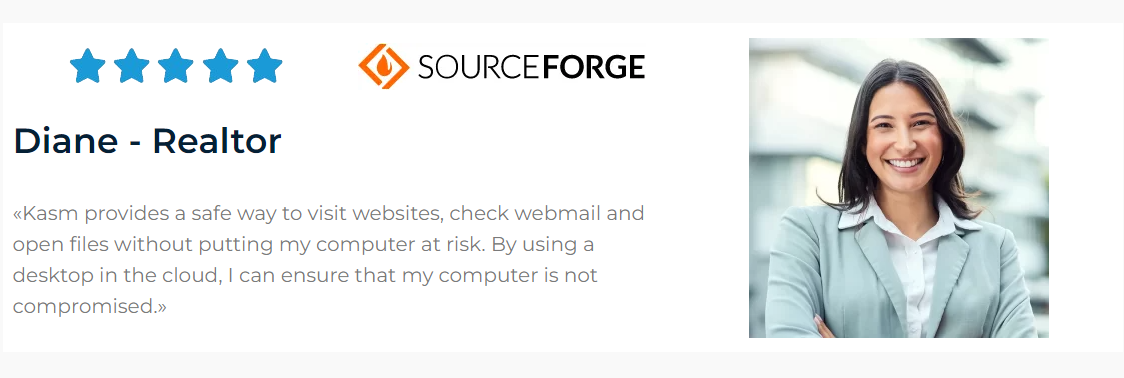
Customer Success Stories



Contact Us


Looking for a Customized Solution?
Explore how CloudVDI Workplaces can enable your web-native remote workspaces.


- +52 55 3155 6749
- Boulevard Manuel Ávila Camacho 36 piso 10, Col. Lomas de Chapultepec, Mexico 11000, CDMX
- luis.perez@neogenesys.com
Solutions
© Copyright 2024 – CloudVDI and Neogénesys. All Rights Reserved.

























